The insider threat is one of the most dangerous and at the same time inherited topics in the field of cybercrime. About cases, when employees of organizations help hackers from the inside, Little is known, And the units are publicly resolved to talk about this. BBC journalist Joe Tidi (Joe Tidy) Read More …
Category: Information security
BlockBlasters: as a patch of popular game turned into a Trojan for theft of data and cryptocurrencies

Dangerous turn for your favorite game 31 July 2025 The years on Steam was a bright 2D platformer/Blockblasters shooter from the Genesis Interactive studio. In the first month, the game received hundreds of positive reviews and quickly won the attention of the audience thanks to dynamic gameplay. However 30 The developers released Augustus Read More …
How to hack and destroy nuclear power 49 minutes: Disassembly of cyber attacks for a nuclear reactor
Late September evening 2023 year. You lazily leaf through ebay. Among the usual junk comes across strange iron - heavy industrial modules. Siemens and Areva logos flaunts on boards. The description is scarce, But professional, The price is amazingly affordable. Here are the components of the TelePerm XS system - Read More …
Steam's alleged hacking is at risk 89 millions of accounts.
What happened? Reported, that data 89 Millions of Steam accounts were at risk due to the alleged leakage, associated with Twilio, service, which Steam uses to send SMS with 2FA codes. Flowing data, Including SMS logs, 2FA codes and metadata, Sold on dark Read More …
The distribution of malicious in Noodlophile under the guise of AI services video generation
Attackers began to use fake video generation tools using artificial intelligence, to spread a new type of malicious software - noodlophile, infostiler, disguised as the result of the work of "AI-services". Fraudulent sites use attractive names, such as Dream Machine, and are actively advertised through large Read More …
ATOMIC Stealer disguise for a hacked version of Evernote: Analysis MacOS attacks
Research Center Ahnlab Security Intelligence Center (Asec) revealed the distribution of the malicious program Atomic Stealer, disguised as the hacking version of Evernote. Atomic Stealer is an information, aimed at MacOS. He steals information from browsers, Key ligaments, cryptocurrencs and system data. Usually it spreads Read More …
Analysis of web browsers telemetry 2025
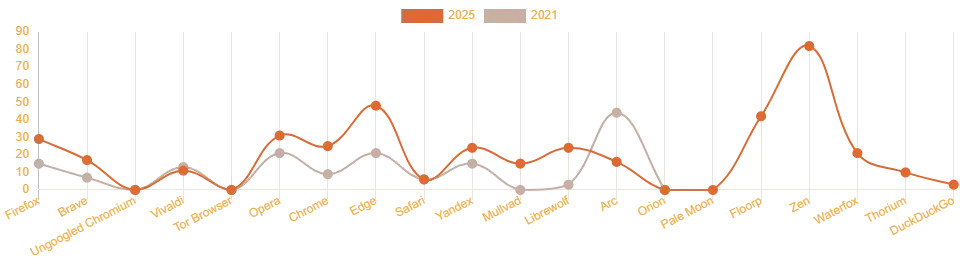
After the publication of the translation of the original article, prepared by the user SIZEOF, Colleagues asked to additionally test several browsers. The purpose of testing was to determine, What outgoing compounds are created after the installation of browsers and at their first launch. Refusal of liability data are provided as it is - without conclusions Read More …
RGB-TEAM “basin” data from PJSC Gazprom
An archive with data from PJSC Gazprom has appeared on the hacktivist website RGB-TEAM. The archive contains three files of ~12 MB: Monitor data relevance, at the moment it is not possible. because. the archive appeared recently and there is practically no analysis data. The account still contains Read More …
Digital detective cheat sheets.

Digital forensics – it's an identification process, conservation, extraction, data analysis and presentation, that have been processed electronically and stored on digital devices. This data, known as digital artifacts, can be found in computers and smartphones and may play a key role in Read More …
Where to store secret files?
All human information can be divided according to importance, like that: Losing files is always unpleasant. That's why we make backups. But the degree to which information security efforts are paranoid depends on the importance. There is a file category, which cannot be lost under any circumstances, even in case of BP. Read More …