All human information can be divided according to importance, like that:
- system backups (importance 1/10);
- current working files (3);
- personal archive: photographs, video (6);
- copies of paper documents (8);
- secrets: keys, passwords, wallets (10/10).
Losing files is always unpleasant. That's why we make backups. Butdegree of paranoia efforts to protect information depend on the importance. There is a file category, which cannot be lost under any circumstances, even in caseBP. These are oursmain secrets, that is, the keys, passwords and wallets.
Like ustold in the previous article, It is advisable to duplicate cold wallets on different drives and store them physically remote from each other, to minimize the risk of loss in a single event.
0. Protected flash drives
A popular option for storing cold crypto wallets is encrypted flash drives such as Digital Bitbox, Safe, Ledger и KeepKey. They automatically encrypt files and have a beautiful display.

Such flash drives (ledgers, trezors) provide additional protection for your crypto wallet. Here we add at least one level of protection:
- PIN code to access the flash drive;
This is in addition to the standard:
- sid-phrase (restoring access to funds in case of loss of wallet);
- password (in addition to the seed phrase).
At the same time, protected flash drives have several disadvantages compared to regular ones.:
- they are more expensive;
- they are more difficult to duplicate for reliability;
- less amount of stored information;
- they attract the attention of intruders.
On the last point. For example, no one will pay attention to an ordinary lost flash drive. But when Trezor is lying on the road, then the finder can contacthacker, who select a PIN code for a reward. And/or will try to find the owner, who immediately becomes a potential victim of extortion. If the “ledger” was found in a person’s personal belongings, on a bunch of keys (For example, during the search) - expect trouble. These are unnecessary risks, which can be avoided. Especially in difficult times, which are coming now.
The advantages of such a beautiful flash drive are rather in convenience and “status” in peacetime. But in reality it might turn out like this, that a person sacrifices his safety for the sake of convenience.
In fact, sellers of such goods make money on people’s fear of losing their wallets. The business model is somewhat similar to antivirus software sellers. The more you fear, the higher the sales.
On the other side, an ordinary cheap flash drive does not cause any suspicion in anyone. The cheaper and dirtier it is, all the better.
Much of the above applies to "password managers", which are a convenient GUI for encrypted storage of randomly generated characters (LastPass, BitWarden, 1Password, KeePass). Yes, it's comfortable. But random character generation and encryption can be done independently using specialized tools. As is the case with protected flash drives, you have to find a compromise between convenience, safety and complexity of procedures, that is, to sacrifice one thing for the sake of another.
1. Encryption
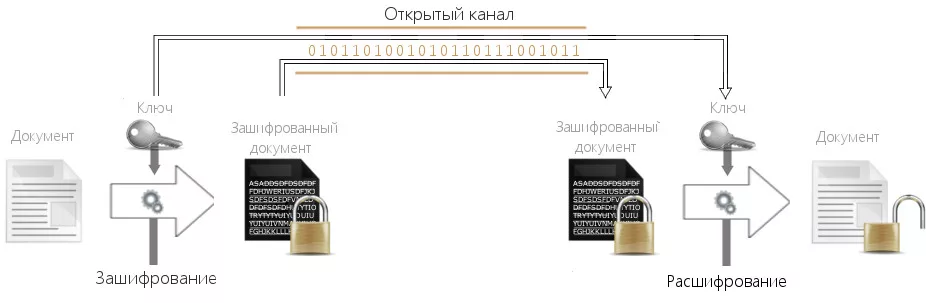
In reality, the best protection is not some magic gadget, and banal mathematics, which we studied at school. Inability to factor the product of large prime numbers. The uniqueness of the coordinates of the intersection of a straight line and an elliptic curve. That is, modern cryptography and encryption.
They say, that all the best in the world is free. Love, friendship, honesty, etc.. Introducing financial calculations often ruins sincere relationships. The same rule applies to cryptographic instruments. Reliable tools are often open source, although there are exceptions here too. Here are some programs for encrypting files and disks for Linux and Windows:
- GnuPG
- VeraCrypt
- Cascade Encryptor
- WinSesame
- AutoCrypt
- Softwinter
- Invisible Secrets
- ccrypt, command line utility
We take secret files - keys, passwords, wallets - we encrypt them and close them with a strong password with maximum entropy.
Then we hide it under the guise of ordinary photos/videos, so that no one will guess that there are secrets. This is steganography - an optional step for additional protection.
2. Steganography + obfuscation
Steganography and obfuscation - hiding encrypted files in an array of other information. For example, in video files or photos.
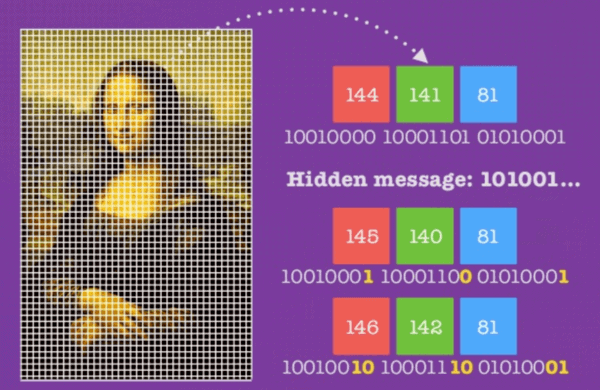
In an ideal situation, no one canprove the fact of the existence of hidden information, until it recognizes the steganography mechanism. It's like Morse code in the blinking of a person on a TV screen. Can't be proven, that there is a useful signal there, until we know the coding scheme, about which the person on the screen agreed in advance with the accomplice.
Suppose, that the bytes of your secret files are written to different pixels of video frames of your home video, masquerading as surrounding colors. For example, Each byte of a secret file can be encoded by adding/subtracting small R values, G, B from neighboring pixels. In the first frame it can be one pixel, in the second frame - another and so on. You can introduce minor distortions into the brightness channel, audio track and other media data. There are a huge number of places in a regular MKV container, where you can easily record your information completely unnoticed.
Without knowing the algorithm for distributing data in the information container, an attacker will not be able to assume that additional data is hidden there. Moreover, even having such an idea will not help the attacker in any way, because there are countless options for obfuscation. It is almost impossible to guess a specific scheme and randomly selected odds. Even if sensitive data is extracted, it will not be possible to decrypt it without a password, so it's double protection.
For optimal protection, it is better to come up with your own version of steganography/obfuscation - and implement it in your own unique way. Surely every person has many ideas, in which files is it better to hide secret bits, so that no one finds them. These do not have to be static files. You can use open Internet traffic as a carrier. For example, add several bits of useful information in every fifth packet from the webcam, similar to what the authors of the advanced SolarWinds trojan did.
Some steganography tools:
- Steghides (JPEG, BMP, WAV, AU).
- Exiftool (writing metadata to file headers, supported196 file formats).
- WavStep (WAV).
- OpenStego (png).
- mp3stegz (MP3).
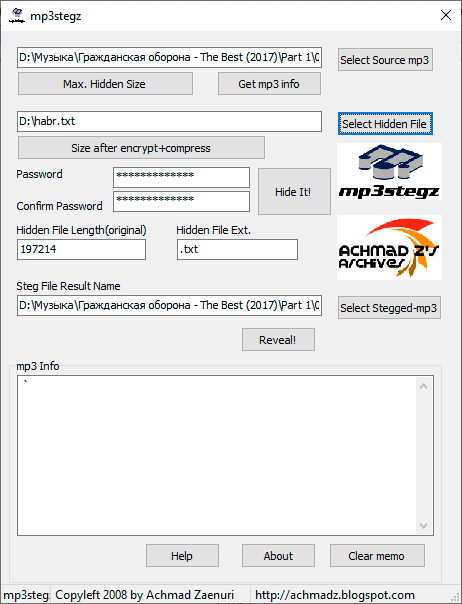
After encryption and obfuscation, the next stage comes - backup..
3. Backup (different continents, different clouds)
If the files are securely encrypted and protected with passwords, then you can store them relatively safely even in public clouds like Google Drive, Yandex.Cloud, Apple iCloud or Telegram unlimited cloud storage (files up to 2 GB).
Of course, with additional security measures, including steganography. That is, secret information is stored under the guise of video files or photographs, dissolved among bits of media content.
As we wrote last time, When duplicating information, conventional backup techniques are used, when each redundancy element reduces the probability of node failure in accordance with the formula:
- where m is the number of reserve elements (reservation ratio);
- q_{i} — probability of failure of element i;
- Q is the probability of failure of a node consisting of n elements (probability of failure of all elements).
Everyone chooses the level of reliability depending on their paranoia: from 99% to 99,(9)%.
Multiple duplication strategies, some of which can be combined with each other:
- different clouds: in case one or more cloud hosting services fail, will go bankrupt, will become unavailable in your country, will delete files for some reason (hosting often has every right to delete user files, according to ToS).
- Various media: SSD, flash drives, CD, DVD and others, with periodic media updates, For example, every 5–10 years.
- Various locations: caches and bookmarks in different cities, countries and continents. Who knows, where fate will take you or your heirs centuries later.
4. Secret Sharing
The latest level of file protection isShamir's secret sharing scheme. It involves dividing the key into a certain number of fragments.
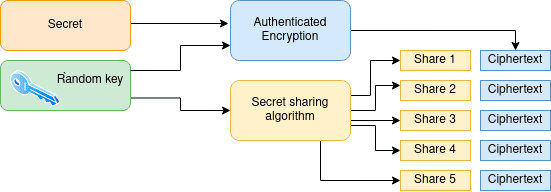
When composing a secret, we can split it into an arbitrary number of fragments (n) and set the minimum number of fragments, which collect the function key (k). For example, n=4, k=3.
The secret sharing scheme satisfies a number of conditions, including:
- The loss of several fragments does not affect the safety of information.
- An attacker gains no information from possessing one key fragment or any number of key fragments, less than necessary (k-1).
Improved option -verifiable secret sharing schemes, such as the Feldman scheme and the Benaloh scheme. They are additionally protected from secret fragment tampering attacks. That is, the algorithm is able to verify the authenticity of any fragment, what is useful.
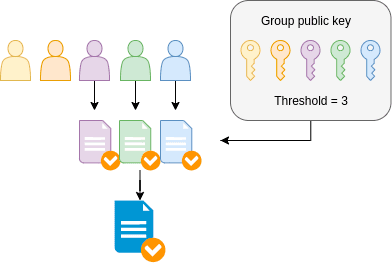
In practice, blockchain can use multi-signatures, that is, multisig addresses. These are the addresses, where multiple keys are required to complete a transaction. For example, 2 from 3 or 3 from 5.
Because no one person is the sole owner of a secret, multisignature increases security level, protecting team members from capture or death of one of them.
Dark Crystal
One of the practical options for sharing a secret can be mentionedDark Crystal. This is a set of protocols, libraries and techniques for securely managing sensitive files, such as keys, wallets and private signatures.
Dark Crystal is designed for implementation in third-party programs and supports any transport protocols. Reference implementations have been developed forJava, Javascript andRust. Reference implementations are implemented based on conventions from the cryptographic librarylibsodium andShamir secret sharing libraries by Daana Sprenklja. Each implementation has a list of modules, which can be freely used.
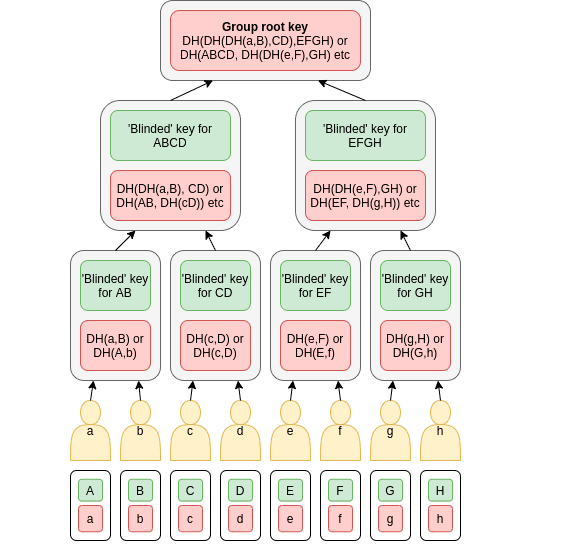
The root group key is divided into parts for reliability (family, Friends, like-minded people)
One of the Dark Crystal modules is the peer-to-peer messenger Briar, which works in the absence of the Internet (Bluetooth, WiFi) and supports secret-sharing multi-signature. Actually, these functions are implemented for itthanks to the integration of Dark Crystal modules.
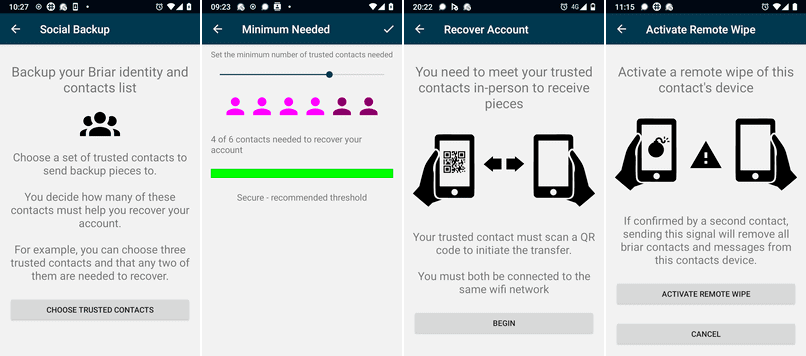
Organization of social backup, selecting users to store private key fragments. On the right screenshot is the menu for activating remote account deletion
Dark Crystal Key Backup protocol has been independently auditedInclude Security, cm.final report based on the results of the inspection.

The photo above shows the procedure for restoring an account and generating a new key.. Initiation requires gathering of users in one place, who received secret fragments from you during a social backup. It could be family members, friends or like-minded people, For example, four out of six people (photo from the reportDark Crystal — Briar Project Case Report).
Sharing the key between relatives allows you to save valuable files, including after the death of the owner. In addition to implementing the will of the deceased, key sharing has other uses. INscientific article with the description of Dark Crystal the following are indicated:
- Social backup.
- Remote removal of secrets (in case a comrade is arrested or kidnapped). Supported by Briar.
- Collective management (making decisions, voting, referendum).
- Re-generation of an individual key in case of loss, through collective voting.
 Procedure for issuing a new key
Procedure for issuing a new key
Conclusion
Summarize. Secure storage of secret files allows for multiple levels of protection:
- Encryption.
- Steganography and obfuscation (hiding the very fact of the existence of encrypted files).
- Duplication on physical drives.
- Duplication on different hostings.
- Key sharing.
You can use individual levels of protection and combine them in almost any combination, depending on the required paranoia in a particular situation.
Discover more from VirusNet
Subscribe to get the latest posts sent to your email.