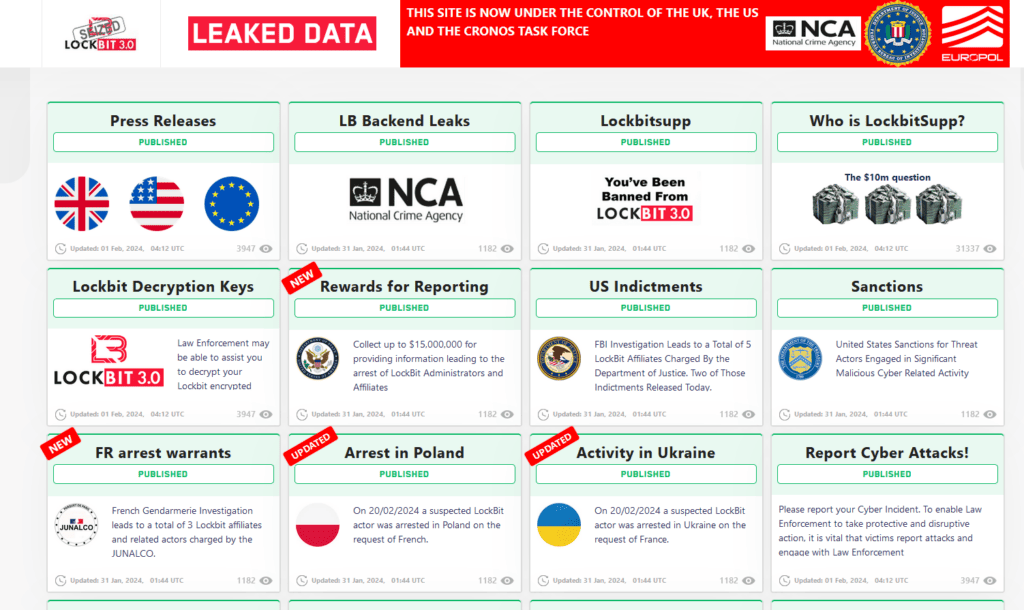
LockBit ransomware infrastructure has been hijacked 20.02.2024 After that, how its dark web leak sites were taken down Monday in a global law enforcement operation codenamed Operation Cronos, which began several months ago and was carried out by the UK National Crime Agency (NCA).
Law enforcement officers managed to obtain the keys and, as a result, through joint efforts, the Japanese police, NCA and Federal Bureau of Investigation (FBI) with the support of Europol, we developed the LockBit decryption tool 3.0 Black Ransomware.
Archive composition
The archive contains two files (note,
- Decryption ID checker (check_decrypt) – the file checks the ability to decrypt your files by checking the identifier against a list of encryption keys obtained by law enforcement officers.
- Check Decrypt for LockBit 3.0 (check_decryption_id) – allows you to evaluate, is there a chance to recover a certain number of files, which were encrypted with LockBit ransomware 3.0. The chances of decryption depend on a number of factors and cannot be predicted without access to the files, encrypted Lockbit. During the assessment process, carried out by the instrument, none of the existing scanned files are modified. But diagnostic data is collected by the tool, which could potentially be useful during additional steps, which (subject to certain conditions) can be implemented in separate stages, involving additional
The functionality is described in more detail in the manual.
https://www.nomoreransom.org/uploads/Decryption_Checker_for_LockBit_Guide.pdf
Details of the operation can be read on the hacked website of the attackers (Tor browser required)
http://lockbitapt2d73krlbewgv27tquljgxr33xbwwsp6rkyieto7u4ncead.onion/
With details, how Lockbit was stopped 3.0 can be read in this report
Discover more from VirusNet
Subscribe to get the latest posts sent to your email.