LinuxCheck– this is a small bash script to collect information, useful for emergency response on Debian and Centos systems. Characteristics: LinuxCheck– this is a separate script, capable of collecting a large set of information: CPU TOP10, memory TOP10 CPU usage boot time Hard disk information User information, information about passwd Read More …
Attention! Victims of the Shade ransomware / Trolldesh / Encoder.858
Dear users. Representatives of the group behind the distribution of the encrypting Trojan Shade/Troldesh/Encoder.858 published all available keys, necessary for decryption (more 750 outside), in the public domain. As well as the software necessary to decrypt files. The message itself Hello. I am writing on behalf of the group, behind Read More …
ASSOCIATION OF COMPUTER AND NETWORK SECURITY CONSULTANTS VIRUSNET
Non-profit voluntary
ASSOCIATION OF COMPUTER AND NETWORK SECURITY CONSULTANTS
VirusNet
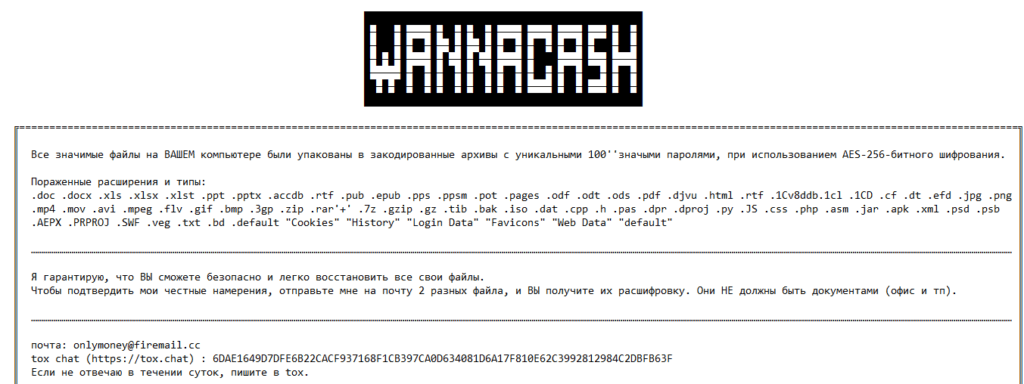
Attention to those affected by WannaCash
How to extract forensic artifacts from pagefile.sys?
Microsoft Windows uses page file (pagefile.sys), for storing memory blocks, which do not currently fit into physical memory. This file, is stored at %SystemDrive%pagefile.sys and is a hidden system file and cannot be read or accessed by the user, including Administrator on active system. This file Read More …
Analyzing compressed memory in Windows 10
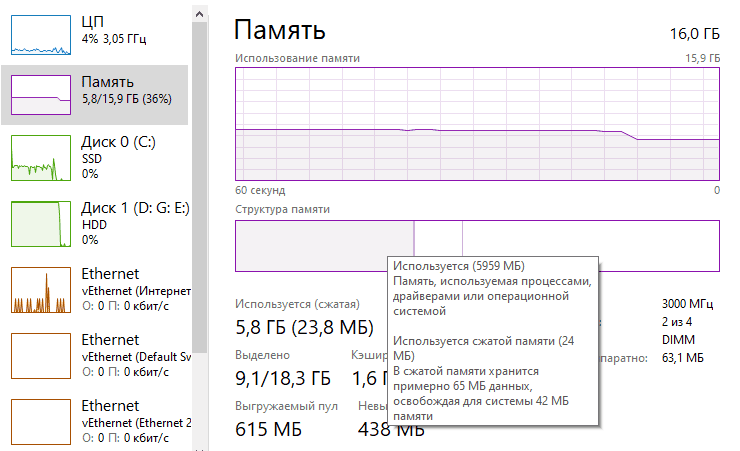
Memory analysis in Windows 10 very different from previous versions of Windows: new feature, called memory compression, makes a forensic tool necessary, capable of reading compressed memory pages. Memory compression in Windows 10 Latest Windows Releases 10 enable memory compression function, which Read More …
Decrypting files after the STOP ransomware
Emsisoft specialists together with ransomware expert Michael Gillespie (Michael Gillespie) released a free decryptor for the STOP Trojan. The utility works with 148 malware variants and will decrypt files, blocked no later than August of this year. STOP ransomware attacks Although STOP is less known, than GandCrab, Dharma and other ransomware Trojans, it accounts for more than half of the detected attacks this year. Read More …
Problems and threats of biometric identification
IN 2018 The law on biometric identification came into force in Russia. Banks are implementing biometric systems and collecting data for placement in the Unified Biometric System (Elementary school). Biometric identification gives citizens the opportunity to receive banking services remotely. This saves them from Read More …
Restoring 1C and Mssql databases after an encryptor attack
Dear users. The S.lab project provides paid services for 1c database recovery (1c7, 1c8 и MSSQL) after a ransomware attack. The cost of the service varies from 10 000 rubles per base, depending on the complexity of the work and the amount of data to be restored. Check and payment:Payment Read More …