The insider threat is one of the most dangerous and at the same time inherited topics in the field of cybercrime. About cases, when employees of organizations help hackers from the inside, Little is known, And the units are publicly resolved to talk about this. BBC journalist Joe Tidi (Joe Tidy) got a rare opportunity to take an inside look at the insider recruitment process, when he himself became the target of a cybercriminal group.
First message: "deal" proposal
In July, the reporter received an unexpected message in the messenger Signal from a certain user under the nickname Syndicate. The stranger immediately offered to cooperate:
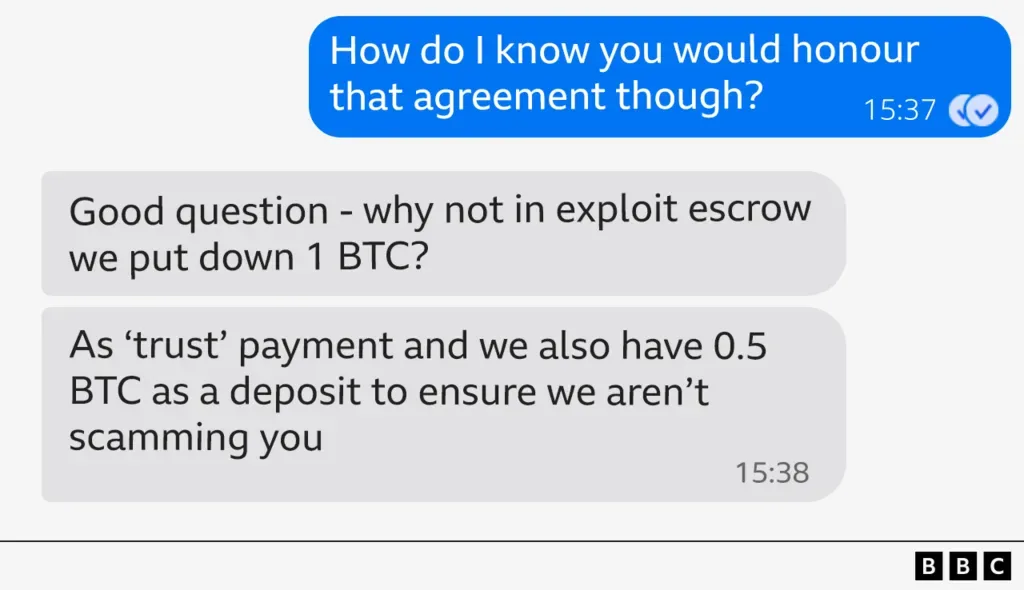
"If you're interested, we can offer you 15% from the ransom amount, if you provide access to your PC".
It was about helping to compromise internal BBC systems: hackers planned to steal data or install malware, and the journalist would receive part of the ransom. After several messages, the “Syndicate” clarified, which can raise the percentage to 25% from the amount of “final negotiations”, promising tens of millions of dollars. The hackers assured, that the target company "won't pay you that much in your lifetime", and cooperation will allow you to “retire right now”.
Attack Scenario
The interlocutor explained, that he needs logins and one-time codes to access corporate systems. Next, the ransomware group planned to introduce malicious software and demand ransom from the BBC in cryptocurrency.
Hackers claimed, that they have already successfully concluded similar “deals” with employees of other companies - a British medical organization and an American emergency response service were named as examples.
It was separately emphasized, that the operation is anonymous: "We will delete this chat, so that you cannot be found".
To strengthen trust, the attackers promised a “deposit” in the amount of 0,5 bitcoin (about 55 000 dollars), if the journalist agrees to cooperate.
Who are Medusa
The interlocutor introduced himself as the group’s “recruitment manager” Medusa - famous gang, working according to the model Ransomware-as-a-service (RaaS). This is a platform, where any partner can rent infrastructure for attacks and share the ransom with the organizers.
According to Check Point, core group, Probably, located in Russia or CIS countries. Medusa avoids attacks on targets in the region, focusing on organizations outside of it. According to official estimates, in four years of operation, Medusa has compromised more than 300 victims around the world.
Pressure and “MFA bombing” tactics
For three days, Tidy feigned interest, consulting with BBC management and collecting information about the methods of the attackers. However, when he began to delay his answer, hackers have switched to more aggressive tactics.
His phone began receiving continuous push notifications asking for two-factor authentication from internal BBC services. This technique is known as MFA bombing: the victim is inundated with requests, until she mistakenly confirms the login and gives attackers access.
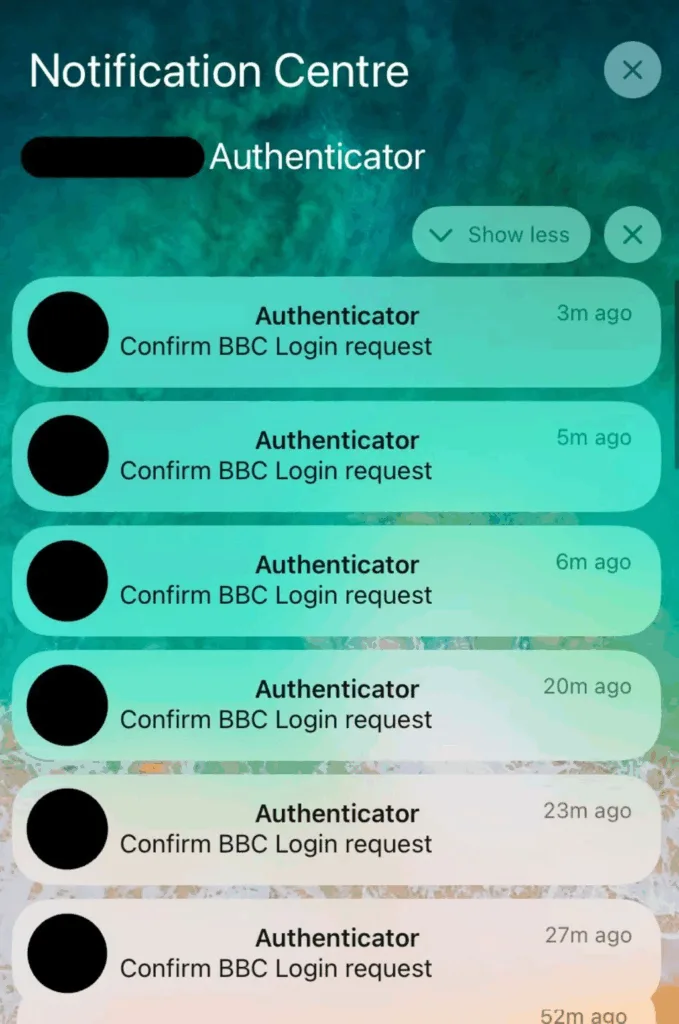
Despite the discomfort and inability to fully use the phone, the journalist did not give in. The BBC cybersecurity team has temporarily disconnected him from all corporate systems., to eliminate the risk of compromise.
Finale and conclusions
After an unsuccessful hacking attempt, hackers sent an apology, calling your actions a “test”. They kept pushing for a deal, But, without receiving a response, deleted their Signal account and disappeared.
The BBC has restored the reporter's access to corporate resources with additional protection measures in place..
What does this mean for organizations?
This case clearly shows, How purposefully do cybercriminals look for the “weak link” within companies?. Key Points:
- Social engineering and financial temptation. Threats or blackmail may not be necessary—an attractive offer of “easy money” is sufficient..
- Ransomware-as-a-service. Modern bands operate as commercial entities, having "recruiters", technical support and public “portfolios” on the darknet.
- Technical pressure. Attacks like MFA bombing are a way to trick the victim into making a mistake and unwittingly granting access.
The BBC experience highlights: insider threats are not an abstraction. Even employees without administrative privileges can be targeted, and successful recruitment threatens millions of dollars in losses and serious reputational damage.
Companies must not only invest in perimeter protection, but also train staff, build channels for trusted reporting of suspicious contacts and apply multi-level authentication methods, capable of withstanding massive attacks.
Discover more from VirusNet
Subscribe to get the latest posts sent to your email.