We continue surfing the web in search of cool cybersecurity stories. And today - an instructive story about, as Amelie Coran (Amelie Koran on her website) I caught a hacker with almost my bare hands, attacking World Bank server, as well as an insider, who tried to play on this story. Having neutralized them, she went after much larger and more dangerous “game”. This story was shared with the public by an English-language podcastDarknetdiaries. Here is a retelling of the episode.

The story is about 2008 year – by the standards of digitalization, the age is not the stone, but still “paper”. So that you understand, how long ago was it: in those days, PalmPilots were still in full use at the World Bank, including – for sending email. Therefore, some methods and programs, which are mentioned in the investigation story, may seem outdated.
A few words about the World Bank, Where, as it turns out, there are also incidents
What kind of organization is this - the World Bank. The host of Darknetdiares specifically explained to his listeners, who are well versed in malicious code, but not in the history of the formation of the global financial system.
The decision to create the World Bank, as well as the International Monetary Fund, was adopted at the Bretton Woods Conference, held in the USA in 1944 year. The bank began active operations in 1945 and set as its goal lending to countries, who needed help in economic recovery, victims of World War II. Thus, Almost the entire recovered post-war world eventually found itself in debt to the World Bank. The lending institution later added initially unreached developing countries to its debtor clientele..
How are these, like Amelie, become "Mr. Wolf", which solves all problems

Before talking about the essence of the incident, a few words about the person, who dealt with it. Amelie Coran graduated from college in 1993, studied programming and sociology. Worked as a user interface designer at Xerox, system administrator, was responsible for the security of the server infrastructure of the American Chemical Society. Truly large-scale tasks awaited Amelie in the company, responsible for the supply of gas and electricity to a number of US states. She didn't have time to get a job there, to the DFIR service (Digital Forensics and Incident Response), how a hurricane hit and knocked out part of the infrastructure. We had to change approaches to designing disaster-resistant data centers on the fly and in the wind, and at the same time learn to work in emergency mode. Amelie developed her experience at Mandiant, specializing in cybersecurity and later at FireEye, one of the world leaders in combating zero-day threats.
Thus, accepting an invitation to work at the World Bank, Amelie imagined, how exactly work is done to ensure information security in large organizations. After working with utility workers, she learned two lessons. First: There is no point in creating an absolutely safe environment, so you need to take care, to make your infrastructure more secure, than the neighbors. Second: accidents happen sooner or later, hence, you can't be hysterical, fall into a stupor. We need to continue to work in conditions of disasters.
In a new place, at the World Bank, these skills came in handy almost immediately.
Incident
The World Bank's file integrity monitoring system detected changes on one of the servers, HSM (Hardware Security Module), in fact, secret “locker” with all banking cryptographic material. The security service found out, that system administrators were not involved in the events, suspected someone from outside.
Amelie Koran was involved in the project as a contractor, she led the investigation. True, this happened two weeks after the server was hacked, when it was difficult to make out, what did the attacker do on the network?, what are the consequences of the investigators’ actions?.
Thrown into the embrasure, Amelie was literally choking in the flow of information. It poured from all sides: from engineers, network administrators and other employees. And this, according to Amelie, it was like trying to hold sand, slipping through one's fingers. There was no way to track the actual actions of the attacker and even just understand that right now he is still on the network, or not.
First, what did they do, – created a complete copy of the infected machine with all its contents, because an attacker can erase his traces or delete some data at any time.
But after studying the logs and notifications of various IT systems, it turned out, that the criminal gained access and changed configurations on more than one, and on thirty servers in the bank! All compromised devices began to be disassembled (in a programmatic sense, not literally) on the cogs, as in the case of the initially discovered hacked server, made copies of them too.
Amelie says, that due to the abundance of information that fell, I felt like a person, who tries to drink from a fire hose. It was sewn up - preliminary analysis of even one car took hours, and dozens of servers were damaged.
The process was slow, and panic grew like a snowball. Emergency meetings were held one after another, management, according to an information security expert, just went crazy, ordinary employees were also extremely tense.

Amelie Coran remembers, like during another crazy conference call, where CIO took part, CISO and other bigwigs, to her, a humble contractor, I even had to shout at them: "Calm down everyone, damn you!"In the original the phrase sounded ruder. She does not feel any regrets for this emotional outburst. Vice versa. One of the main tasks of a specialist in complex incidents, she thinks, bring at least some semblance of order to the situation, when people's ears are already steaming from stress. Neither high IQ, no deep knowledge of cyber investigations can replace a cool head.
Yesterday in the office, and tomorrow - in the newspaper!
Ordinary bank employees were not aware of the details of the incident, but somehow the press found out about them. Wall Street Journal Edition, and then Fox News reported, in particular, that the World Bank is experiencing an "unprecedented crisis", referring to the letter from the technical director. That, that the situation has become public, added nervousness. But most importantly, attacker, if you weren't already aware, found out, that he was discovered.
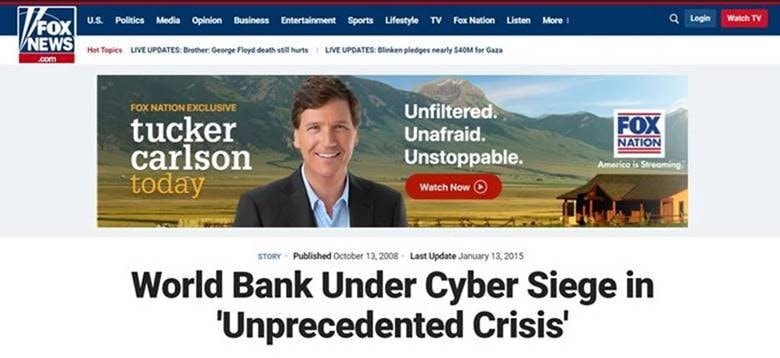
Only an insider could leak information. Technical details about the timing of the attack, affected servers, which were also leaked to the press, knew a very limited circle of people. Those, who took part in the “war councils”.
Amelie began to compile a list of possible moles, First of all, I started to look closely at IT specialists and top managers. She studied quotes from articles and patiently searched for something similar in the correspondence of the main suspects (the expert does not give details, but apparently in 2008 she carried out this analysis manually, she didn’t have any DLP systems to help her). Gradually, the members of the investigation team themselves, and top managers began to “look askance” at each other -how in the game Among us. “Military Council” turned into a battle of views, when everyone tried to discern an internal enemy in one of their colleagues.
While non-professionals suspected everyone they met, Amelie narrowed her circle of possible insiders to five or six people. She was inclined to think, that the insider is not present at closed meetings, but, Maybe, attracted to some more or less open part. To check the version, Amelie staged a provocation: planted documents with false information in the meeting room, I attached a few to the information board.
Setting up surveillance of corridors and offices, looking through, who exactly is sitting at the computer? (it had to be done this way, literally spying on the staff), investigation officers discovered a possible insider. His connection with the media was fully confirmed a few days later, when an article with fake information was published.
Large fish
An insider's PC hard drive was fingerprinted. Using EnCase for this (forensics tool) and some other tools, the expert discovered, that the employee sent letters to the media via Yahoo webmail, and not through corporate Lotus Notes.
At the same time it turned out, that the insider was connected to the former head of the World Bank, Paul Wolfowitz (Paul Wolfowitz). It’s worth telling a little more about this person.. Paul's candidacy as head of the World Bank was not suggested by anyone, and US President George W. Bush personally. This caused confusion among financial journalists, since Paul's previous position was Deputy Secretary of Defense. Is it true, Paul was not fired because of a financial or military scandal, but because I got my friend a job at the bank.
Paul Wolfowitz did not forget the insult and took advantage of the moment and decided to discredit the new leadership, sending compromising information to the media. To collect it, he decided to recruit a specialist from the internal investigations department. He was gay, but did not advertise this fact. More than ten years ago this could have been used as leverage. The recruited employee, in turn, forced the IT specialist to work for him, who helped collect the necessary information. And it was he, as we already know, fell for Amelie's bait.
Thus, one of the problems - leaking information to the media - was solved. Amelie, unraveling one tangle, was able to spend the night at home for the first time in many days, not on the blanket under the table, where have you been working lately?. Sleep under the table, according to her, it's still a pleasure.
How and why the criminals “entered” the bank?
Hacker, who was digging on the servers, still hasn't been discovered. But it became clear, how exactly did he penetrate the information system. It didn’t work out right away. The hacker managed to penetrate one of the computers, launched malicious code, but it was blocked by the antivirus. The criminal tried another vulnerability - it worked, antivirus did not respond. The attacker developed an attack and gained access to password hashes. With their help I hacked the system administrator account.
Amelie decided to check, How weak is the system administrator’s password and how long will it take to crack it?. It revealed, that you can find out the password of such a responsible bank employee in just a few minutes, which Amelie told management about. She also guessed, that this is a systemic problem, asked the administrator to update the password and write it down on paper. After that, I launched a password audit program and cracked a new one in a few minutes. Same as previous passwords, he was uncomplicated: it was the name of the manager's daughter with the year of her birth.
The bank has revised its password policy, improved access control policies, and a few months later they invited specialists from Microsoft, so that they conduct an independent audit of the situation with AD and passwords throughout the bank.
So who needed to hack the World Bank??
This part of the story has the least details, but this is what investigation data Amelie Coran was able to reveal. It revealed, that hackers were actively seeking access to databases, which were used by the heads of the HR department. I'm talking otherwise, the attackers were interested in the names of specific bank employees. Mandiant specialists, connected to the study of malicious code, used our new Mirror tool for analysis. Based on the totality of information collected, the management of the World Bank was able to conclude, that the attackers, more likely, – Chinese hackers.
At the end of the story about the investigation, Amelie shared her impression of the feeling of working on such a large project: "While you are struggling with technical problems, you have adrenaline too, and endorphins, and sense of self-worth. But when the political or economic background is revealed, then you discover, that you are part of another, an even more complex game".
Source