Assembly and handwriting. For the purpose of analysis, the source code was taken, leaked to the public on October 10, 2023. The program is written in C++ (uses the C++17 standard and supports Windows XP) and was assembled on MSVS 2015. Project file tags indicate the creation of source code on a Russian-language OS. Read More …
Cloudflare's DDoS protection was bypassed
Protection Mechanisms, configured by Cloudflare customers (For example, firewall, preventing DDoS attacks) for websites, may be bypassed due to gaps in firewall security controls, potentially exposing clients to attacks, which Cloudflare should prevent. Attackers can use their own Cloudflare accounts to abuse trusted relationships Read More …
New decryptor from Avast: solving the problem with the Fonix/Ryuk ransomware
phoenix (or Ryuk) – malware, encrypts files on a computer, named after the Japanese manga character Death Note. Attacks, using this ransomware, are becoming more common, and it is almost impossible to decrypt files without a special key. Avast has released a new version of the decryptor for Read More …
File decryption available after CryLock 2.0.0.0, 1.9.2.1 and 1.8.0.0
Dear users, it is now possible to decrypt files encrypted by some versions of CryLock versions 2.0.0.0, 1.9.2.1 and 1.8.0.0. The resulting keys are guaranteed to match the email files: In other cases, analysis of the encrypted file is required. There are no keys to decrypt email files yet: For getting Read More …
Archive recovery, Acronis images and virtual machines, mail program databases after a ransomware attack
Dear users. The shifru.net project provides paid services for recovering the following types of files after a ransomware attack: rar and zip archives; Acronis images, veeam, windows backup; images (hard disks) virtual machines; mail program databases (exchange, outlook, bat, mozilla thunderbird). Check and payment:Payment is made upon completion of work Read More …
Avast released decryptor for decryption after Babuk ransomware.
Czech cybersecurity software company Avast has created and released a decryption tool, to help Babuk ransomware victims recover their files for free. According to Avast Threat Labs, Babuk decryptor was created using leaked source code and decryption keys. Free Read More …
Decrypting files after Fonix ransomware
The authors of the ransomware abandoned malicious activities and published the master key. And we made a decoder out of it. The authors of the Fonix ransomware suddenly announced the cessation of their activities and published the master key, which can be used to decode affected files. Our experts immediately updated the Rakhni Decryptor utility to automate this process. Read More …
Attention to those affected by [[email protected]].5D3d
According to S.Lab, this ransomware does not encrypt files, but destroys them (fills with zeros). What makes it impossible to decrypt/recover them?. If you decide to pay a ransom to criminals (which is absolutely not recommended to do), then make sure, that the files are encrypted, not destroyed.
PoSH-R2 script for collecting various diagnostic information
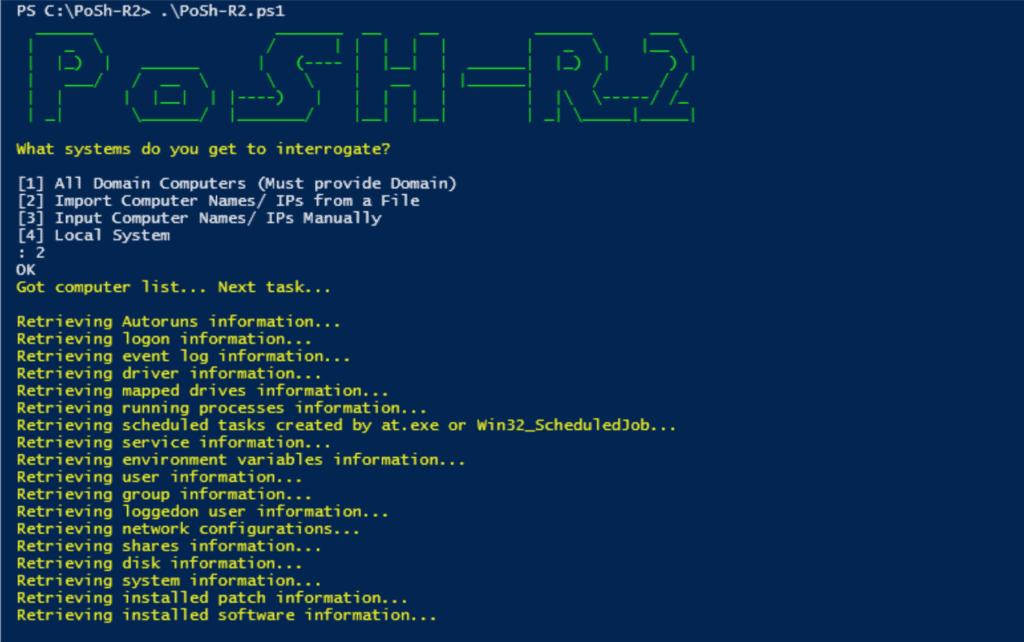
Description PoSh-R2PowerShell – this is a set of powershell scripts for Windows Management Instrumentation (WMI), which investigators and forensic analysts can use to extract information from compromised (or potentially compromised) Windows systems. The scripts use WMI to extract this information from the operating system. Hence, this Read More …
Attention to victims of the WannaCash ransomware (v170720 and v010820)

Dear users, thanks to FKLK user safronov, who provided for analysis a program for decrypting WannaCash encrypted files, It's now possible to decrypt your files free of charge. To get help, you need to contact the profile section on the forum. And don't forget about the request rules Read More …