Description
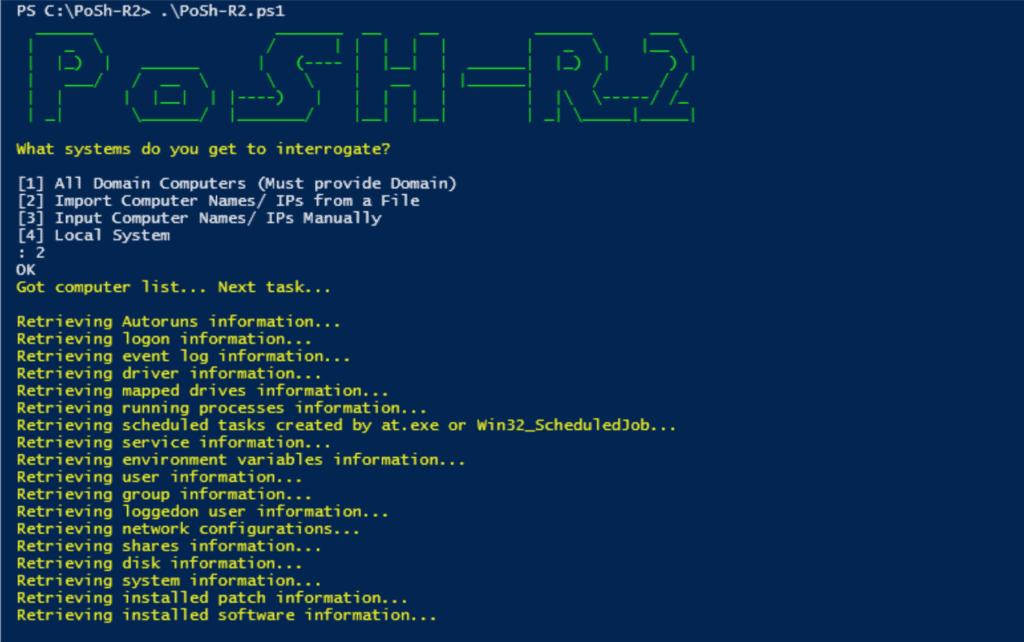
PoSh-R2PowerShell – this is a set of powershell scripts for Windows Management Instrumentation (WMI), which investigators and forensic analysts can use to extract information from compromised (or potentially compromised) Windows systems. The scripts use WMI to extract this information from the operating system. Hence, this script will need to be run on the user, having the necessary privileges, and authentication is performed through network login. The received data is written to CSV and SQLite databases in the system, in which the script was run.
PoSH-R2 can obtain the following data from an individual machine or group of systems:
– Autorun entries
– Disk information
– Environment Variables
– Event logs (50 latest)
– Installed software
– Login sessions
– List of drivers
– List of mapped network drives
– List of running processes
– User, logged in
– Local groups
– Local user accounts
– Configuration
networks – Network connections
– Patches
– Scheduled Tasks Using AT Command
– Shared Resources
– Services
– System information
Application
- Run the script from a PowerShell window with the appropriate permissions for WMI and follow the instructions.
- The data will be saved in a new directory called "PoSH_R2 – Results" in the same directory, from which this script was executed.
This script will work with PowerShell version 2 and higher.
You can download the script at this page