During forensic analysis of a Windows system, it is often important to understand, when and how a specific process was started.
To identify this action, we can extract a set of artifacts from the target system, useful for collecting evidence of program implementation.
UserAssist
On a Windows system, all GUI-based programs, launched from the desktop, are tracked in the following registry key:
HKEY_CURRENT_USERSOFTWAREMicrosoftWindowsCurrentVersionExplorerUserAssist{GUID}\Count
Entries contain two GUID subkeys ( Executing the CEBFF5CD executable, The executable file label is F4E57C4B ): each subsection maintains a list of system objects, such as programs, Control Panel Shortcuts and Applets, which the user contacted.
The registry values in these subkeys are encrypted using the ROT-13 algorithm, which basically replaces a character with the position of another character 13 from it in the ASCII table.
All values are ROT-13 encoded, For example:
.exe = .RKR
.lnk = .CLOSE
Background Activity Moderator (BAM)
BAM – this is a windows service, which monitors the activity of background applications.
This service appeared in Windows 10 only after the Fall Creators update – version 1709
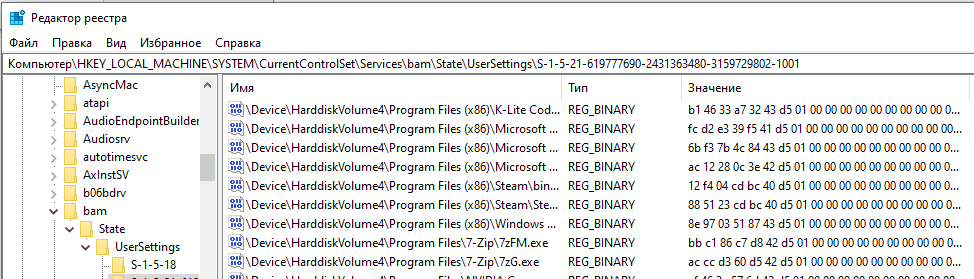
It provides the full path to the executable file, which was running on the system, and also the date / last execution time and is located in this registry path:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesbamStateUserSettings{SID}
Branches contain a list of paths and executable files, and the value of each of them is the last execution time in Filetime format (64-little endian bit method) в UTC:
RecentApps
!Valid up to Windows version 10 assemblies 1803 (not inclusive)
Program Execution, running on Win10 system, tracked in the RecentApps key:
HKCUSoftwareMicrosoftWindowsCurrentVersionSearchRecentApps
Each GUID key points to a recently launched application:
AppID = Application name
LastAccessTime = Last execution time in UTC.
LaunchCount = Number of starts
ShimCache
Windows Application Compatibility Database used to identify possible application compatibility issues with executables and tracks the filename of the executable, file size, last modified time.
Posts about the latest 1024 executed programs in the OS are stored in the parameter CacheMainSdb:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSession ManagerAppCompatCache
HKEY_LOCAL_MACHINESYSTEMControlSet001ControlSession ManagerAppCompatCache
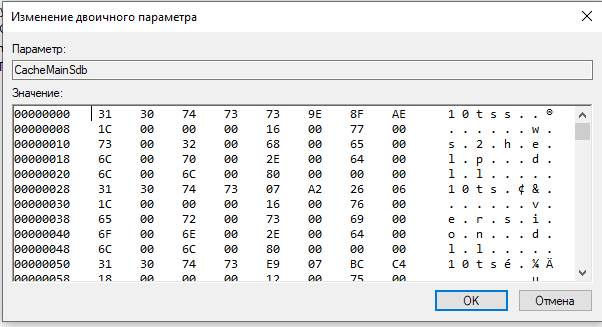
You can use this key to identify systems, which were running specific malware, using a special tool, such as ShimCacheParser.py , от Mandiant (https://github.com/mandiant/ShimCacheParser)
Notes on the parameter CacheMainSdb
- For Windows 7/8/10 parameter contains no more than 1024 records
- LastUpdateTime does not exist on Win 7/8/10 systems
Amcache
ProgramDataUpdater (task, service related Application Experience) uses file Amcache.hve to store data about the first execution of the program (even portable from removable media). The file is located:
c:\WindowsappcompatProgramsAmcache.hve
The file can be analyzed using the plugin amcache for the program RegRipper (https://github.com/keydet89/RegRipper2.8)
For more information aboutAmcache andShimcache in forensic analysis, Please, refer to this article: Amcache and Shimcache in forensic analysis
Jump Lists (jump list)
Windows taskbar 7-10 (jump list) designed for, to allow users to "navigate" or access elements, that they have used frequently or recently.
The data is in the folder:
%USERPROFILE%AppDataRoamingMicrosoftWindowsRecentAutomaticDestinations
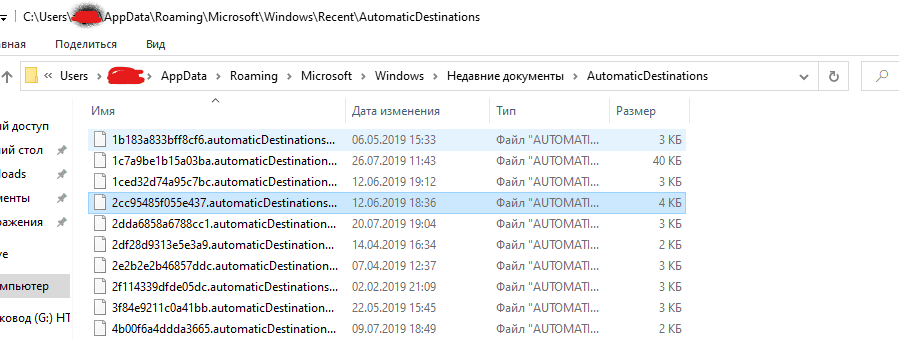
Each entry is a unique file with the addition AppID relevant application.
AutomaticDestinations jumplist files are OLE Compound Files, containing multiple threads, of which:
- hexadecimal number, For example, "1a"
- list
Each of the hexadecimal numbered files contains data, similar to Windows shortcut data.
Data can be extracted and analyzed using a parserLNK, for example lnk-parse (https://github.com/lcorbasson/lnk-parse).
Prefetch
Windows preboot files are designed to speed up the application startup process. Prefetch files are stored in the folder
%windir%Prefetch
and contains the name of the executable file, list of Unicode DLLs, used by this executable, counter of the number of executions of the executable and timestamp, indicating the last time the program was run.
This folder stores data about the latest 128 executable files on Win7 and latest 1024 on Win8-10.
Preliminary filesamples can be analyzed and analyzed using such tools, HowPeCMD (https://github.com/EricZimmerman/PECmd).
Discover more from VirusNet
Subscribe to get the latest posts sent to your email.