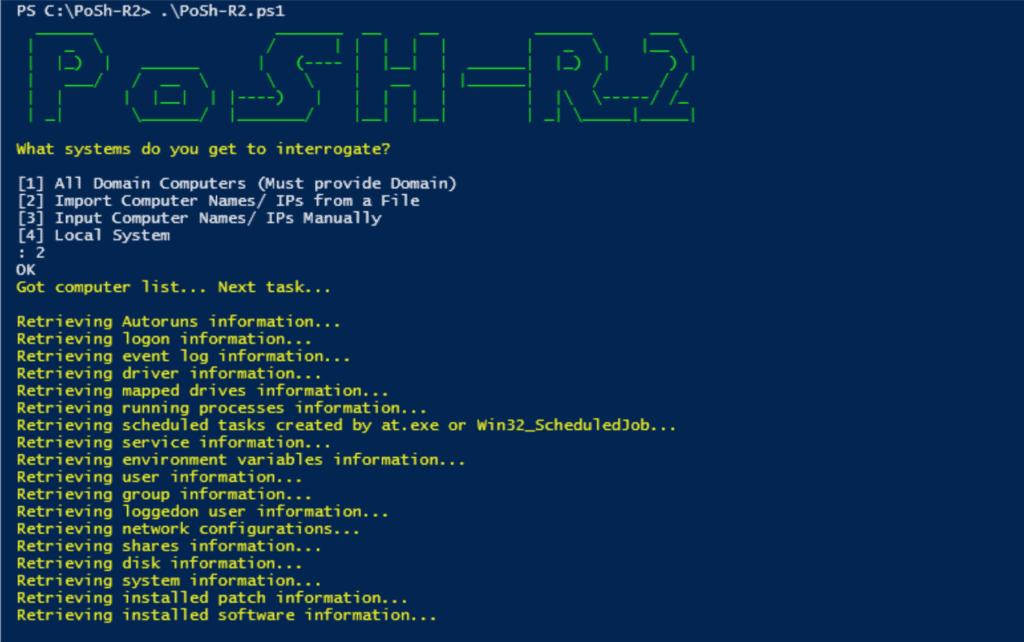
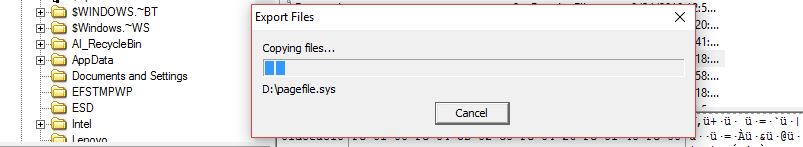
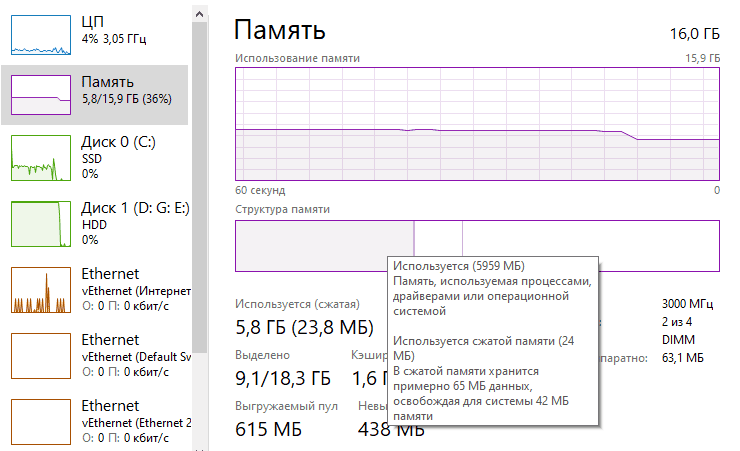
Digital forensics – it's an identification process, conservation, extraction, data analysis and presentation, that have been processed electronically and stored on digital devices. This data, known as digital artifacts, can be found in computers and smartphones and may play a key role in Read More …