An archive with data from PJSC Gazprom has appeared on the hacktivist website RGB-TEAM. The archive contains three files of ~12 MB: Monitor data relevance, at the moment it is not possible. because. the archive appeared recently and there is practically no analysis data. The account still contains Read More …
Category: Blogs
Blog about things familiar to most people, from a non-standard point of view.
How a hacker and an insider were caught at the World Bank
We continue surfing the web in search of cool cybersecurity stories. And today - an instructive story about, as Amelie Coran (Amelie Koran on her website) I caught a hacker with almost my bare hands, attacking World Bank server, as well as an insider, who tried to play on this story. Having neutralized Read More …
Digital detective cheat sheets.

Digital forensics – it's an identification process, conservation, extraction, data analysis and presentation, that have been processed electronically and stored on digital devices. This data, known as digital artifacts, can be found in computers and smartphones and may play a key role in Read More …
Windows XP: puzzle title.wma
Old operating systems and applications can still surprise. Every file sometimes hides a whole story.. Who is the real author of the Pinball Space Cadet demo game and is it true Bliss desktop wallpaper ("Serenity") were filmed in Sonoma County, State of California? Similar Read More …
Browser war. Netscape
The Internet is an amazing invention of mankind, and we're used to it, that it is also free. Yes, Certainly, we all pay to connect, creation and maintenance of websites, but Internet surfing itself never demanded money from us, and Internet access via browsers Read More …
Where to store secret files?
All human information can be divided according to importance, like that: Losing files is always unpleasant. That's why we make backups. But the degree to which information security efforts are paranoid depends on the importance. There is a file category, which cannot be lost under any circumstances, even in case of BP. Read More …
Anonymous search networks. DuckDuckGo Review.

DuckDuckGo– it is a famous open source search engine, which declares, that it does not track or store personal information of its users. This is independent, which “tired” from online tracking. As the company itself declares: We help protect your privacy with our free browser, which can Read More …
Analysis of the HelloKitty ransomware source code
Assembly and handwriting. For the purpose of analysis, the source code was taken, leaked to the public on October 10, 2023. The program is written in C++ (uses the C++17 standard and supports Windows XP) and was assembled on MSVS 2015. Project file tags indicate the creation of source code on a Russian-language OS. Read More …
Cloudflare's DDoS protection was bypassed
Protection Mechanisms, configured by Cloudflare customers (For example, firewall, preventing DDoS attacks) for websites, may be bypassed due to gaps in firewall security controls, potentially exposing clients to attacks, which Cloudflare should prevent. Attackers can use their own Cloudflare accounts to abuse trusted relationships Read More …
PoSH-R2 script for collecting various diagnostic information
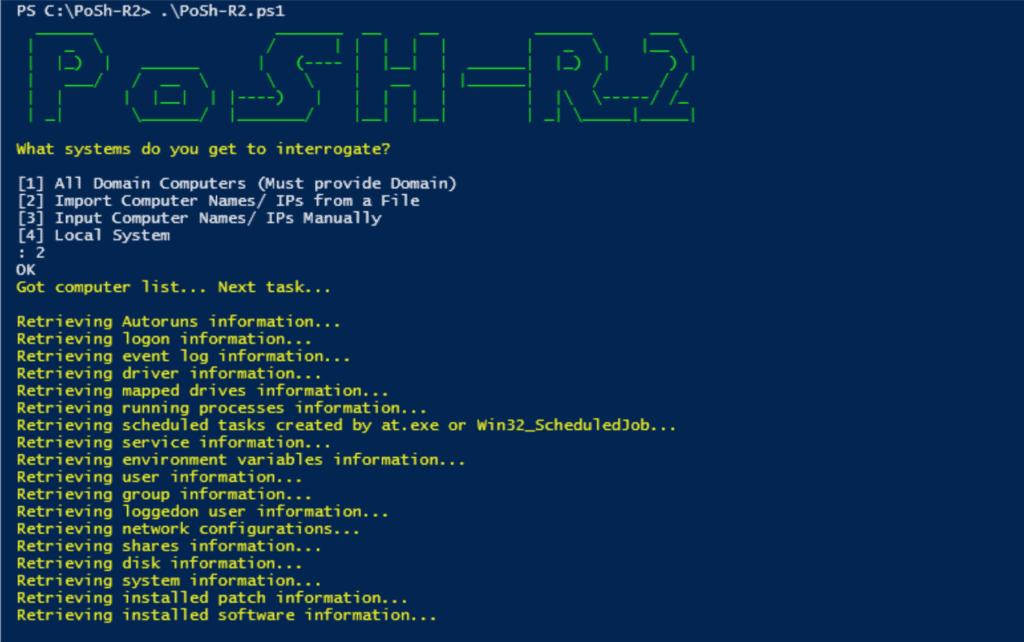
Description PoSh-R2PowerShell – this is a set of powershell scripts for Windows Management Instrumentation (WMI), which investigators and forensic analysts can use to extract information from compromised (or potentially compromised) Windows systems. The scripts use WMI to extract this information from the operating system. Hence, this Read More …