Data from Amcache and Shimcache can provide a timeline of whether, what program was executed, when it was first launched and last modified.
Forensic Artifacts: proof of program execution on Windows systems
During forensic analysis of a Windows system, it is often important to understand, when and how a specific process was started.
Attention! Victims of the [email protected] ransomware
Decrypting files after WannaCash ransomware (.punisher)
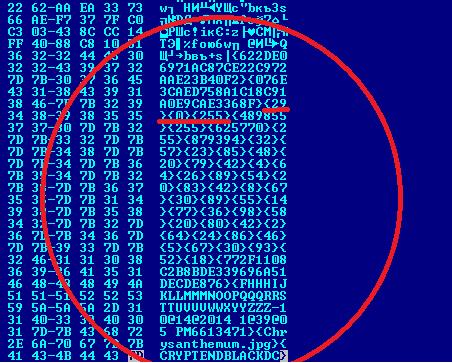
Decoding some versions of Cryakl
Specialists and Internet resources of the VIRUSNET ASSOCIATION
Current list of resources and users included in the Association.
Charter of the VIRUSNET Association
Non-profit voluntary
ASSOCIATION OF COMPUTER AND NETWORK SECURITY CONSULTANTS
Decrypting files after cryakl ver-CL 1.5.1.0
note: Transcription service is provided free of charge on a first-come, first-served basis..
Mail hacking or porn blackmail on $864
Fraudsters are becoming more sophisticated, Porn blackmail is now trending, when the user receives a sent message “on behalf of” your own mailbox with content: Hello! I’m a hacker who cracked your email and device a few months ago. You entered a password Read More …
A story about an abnormally high electricity consumption computer at one enterprise…
An old friend calls me. Speaks, help! The server at work went crazy – consumes so much electricity, but for a legal entity it is expensive… Sysdamin hasn't been able to figure it out for so long, a lot, They even bought him new spare parts, everything is useless. And from the side Read More …